Secret Management
How do you manage your app’s backend secrets?
- Hardcoding secrets and committing them to git? 😨
- Manually populating a local .env file with every repo clone? 😑
- Or using a centralized secret management service? 👌
What is a secret?
To ensure we’re on the same page: a secret is simply a piece of sensitive information used for authentication or authorization - think API keys, passwords, connection strings, etc.
Random note: UUIDs are not considered secrets. They are not secure enough.
And a friendly reminder: hardcoding secrets in your code is a major no-go.
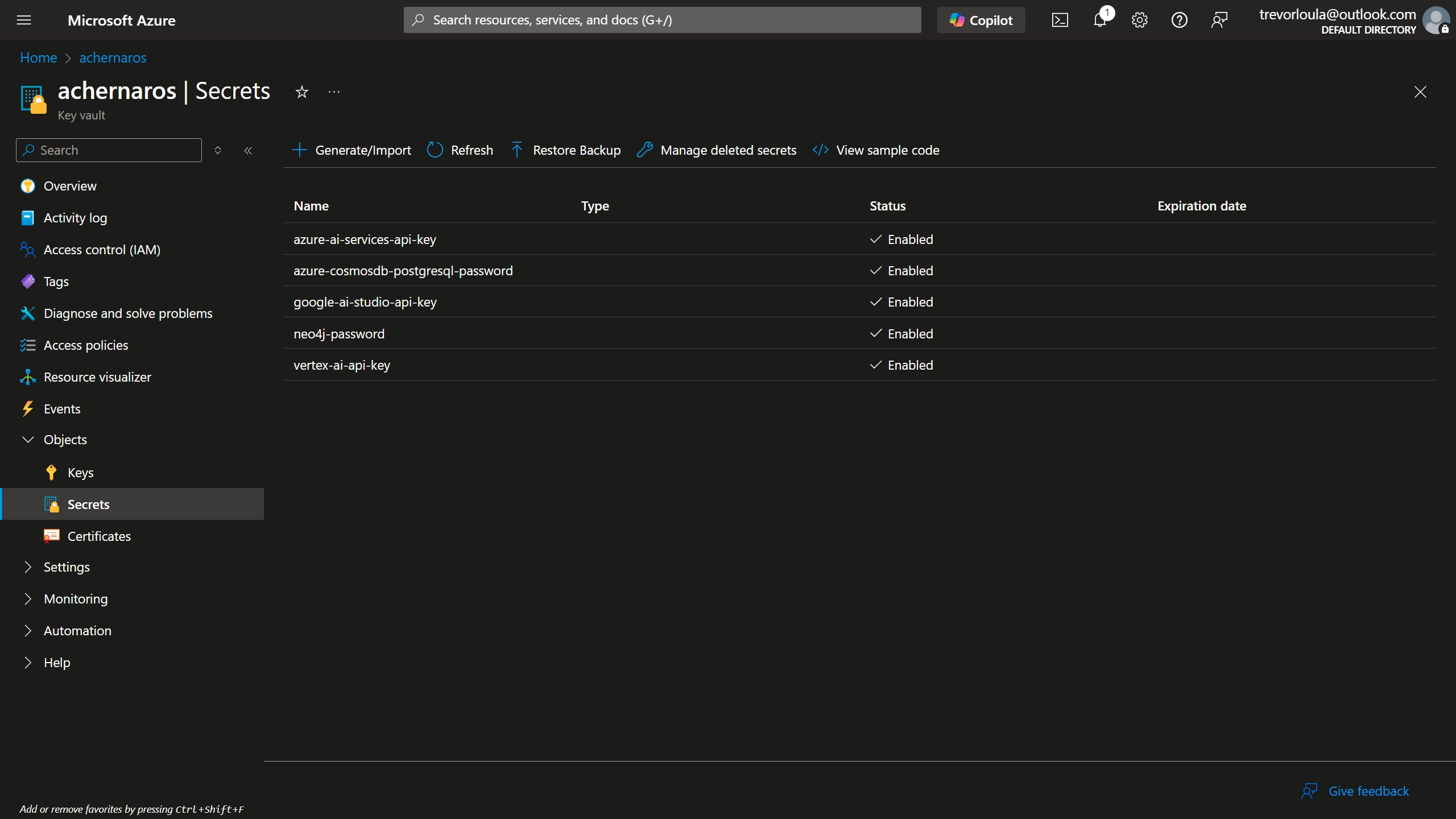
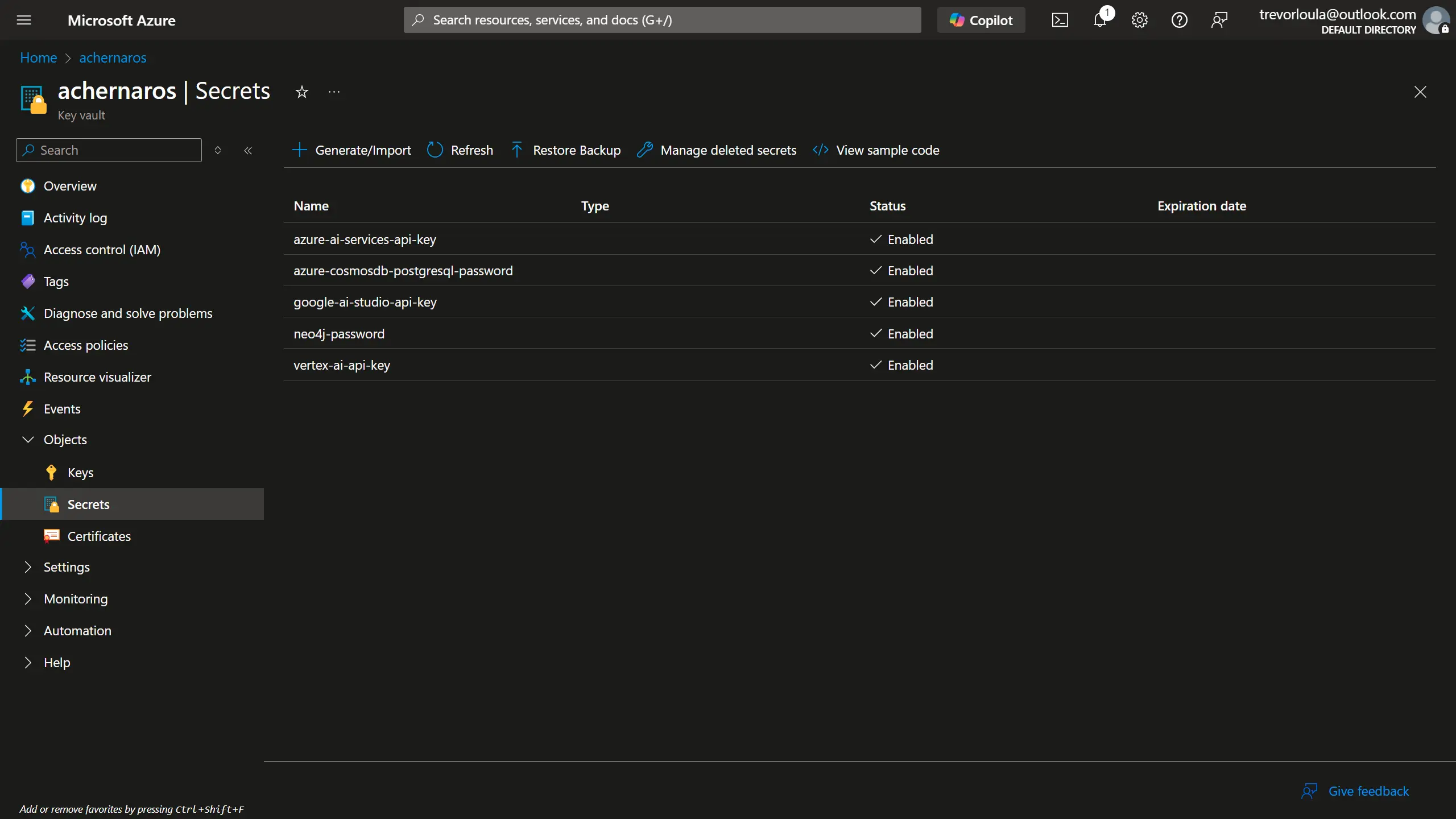
Secret Management Services
A secret management service offers you a secure, centralized spot to store all your secrets. Major cloud providers offer their own solutions:
Your app simply needs to authenticate with the secret management service, and then it can easily retrieve all its secrets.
Platform Managed Credentials
Static secrets have some big drawbacks:
- Rotation difficulties: Changing a secret quickly and regularly can be a real hassle.
- Lack of expiration: They usually don’t automatically expire. Which means if compromised, they grant indefinite access until rotated.
Enter platform managed credentials. Rather than using a static key, you let your app use role-based access control to request short-lived tokens (generally 1 hour). For example, rather than giving your app a permanent storage account key, you can configure your cloud provider to issue a token after verifying your app’s identity. This way, even if a token is compromised, its short lifespan limits the risk.
Tokens
JSON Web Tokens (JWT) are a compact way to authenticate between services without over-relying on static secrets. A JWT typically has three parts:
- Header: Basic info about the token type and the algorithm used.
- Payload: Contains claims, such as user identity or service roles.
- Signature: Verifies the token’s integrity using a secret or key.
In practice, an Authorization Server (like Azure Entra, Auth0, or Clerk) issues these tokens after verifying credentials, while a Resource Server (such as Azure Storage or Azure Key Vault) validates them before granting access.
This token mechanism helps manage secrets by eliminating the need for long-lived, hardcoded credentials. Instead, services exchange short-lived tokens, reducing risks if a token is compromised.
Auth Flow
Authentication can feel like a chicken-and-egg problem - you need a secret to access your secrets. Here’s my approach for authentication with a secret management service:
- Development: My app runs locally and uses my developer credentials (e.g., via the Azure CLI).
- Production: My app runs in the cloud and leverages a platform managed credential (like Azure’s managed identity).
By combining platform managed credentials with a secret management service, you can keep static secrets out of your codebase and environment variables entirely.
Best Practices
-
Evaluate Credential Options First: Before creating a secret, check if you can use platform managed credentials instead. If you’re authenticating between services within the same cloud provider, this should be possible. For third-party API interactions, this generally isn’t feasible and you’ll have to settle for a secret.
-
Enforce the Principle of Least Privilege: When creating a secret or a role assignment, assign only the minimum privileges required. For example, if your app needs to read images from a storage account, it should only have read permission on your
/imagescontainer. It should not have read/write access to both/imagesand/sensitive-data. Grant only what is needed. Developers often overprivilege during initial development and forget to tighten security later. Start lean to mitigate potential risks and save yourself a headache later. -
Keep Secrets Out of Logs: Always ensure your secrets remain secret. Avoid logging them or assigning them to variables that might be captured by your logging infrastructure.
Conclusion
Secret management is a crucial part of modern software development. By leveraging platform managed credentials and a secret management service, you can keep your app secure and your codebase clean.
← Back to blog